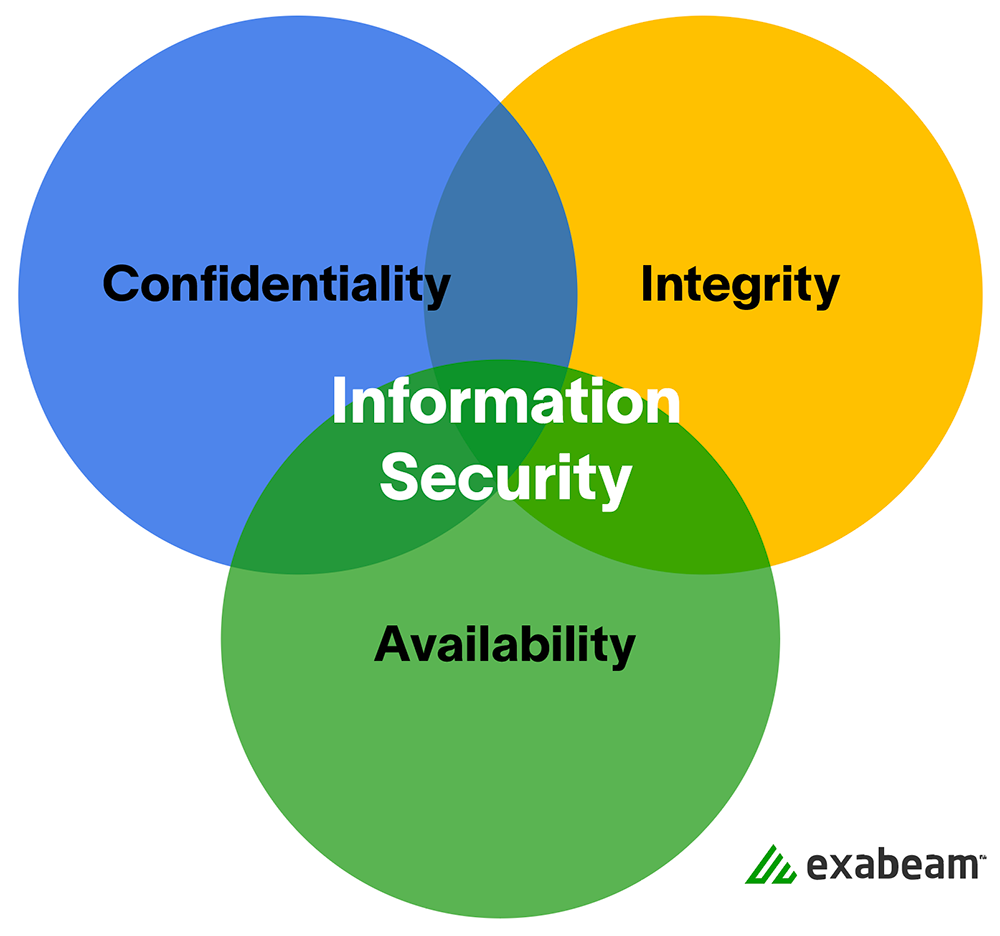
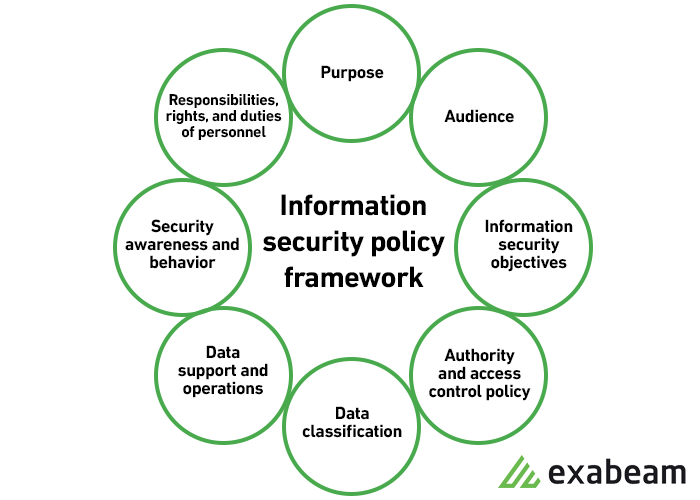
Information Security Policy Quick Reference Guide to Data Classification and Secure Data Handling - IT Help

Statement of Policy by the National Security Council on Basic National Security Policy | Teaching American History
9 policies and procedures you need to know about if you're starting a new security program | CSO Online

TEMPLATE Information Security Awareness and Training Policy | PDF | National Institute Of Standards And Technology | Information Security